Reveal the LinkDaddy Universal Cloud Storage Press Release for Trick Insights
Wiki Article
Maximizing Data Safety And Security: Tips for Getting Your Info With Universal Cloud Storage Space Provider
By carrying out robust information safety and security actions, such as file encryption, multi-factor authentication, routine backups, accessibility controls, and keeping an eye on protocols, customers can dramatically enhance the protection of their information saved in the cloud. These approaches not just fortify the stability of details however likewise infuse a sense of confidence in delegating important data to cloud systems.Relevance of Data File Encryption
Information file encryption acts as a fundamental pillar in securing delicate info stored within global cloud storage services. By encoding data as though just accredited events can access it, security plays a crucial function in securing secret information from unauthorized access or cyber threats. In the world of cloud computer, where information is commonly transferred and kept across various networks and web servers, the need for durable encryption devices is extremely important.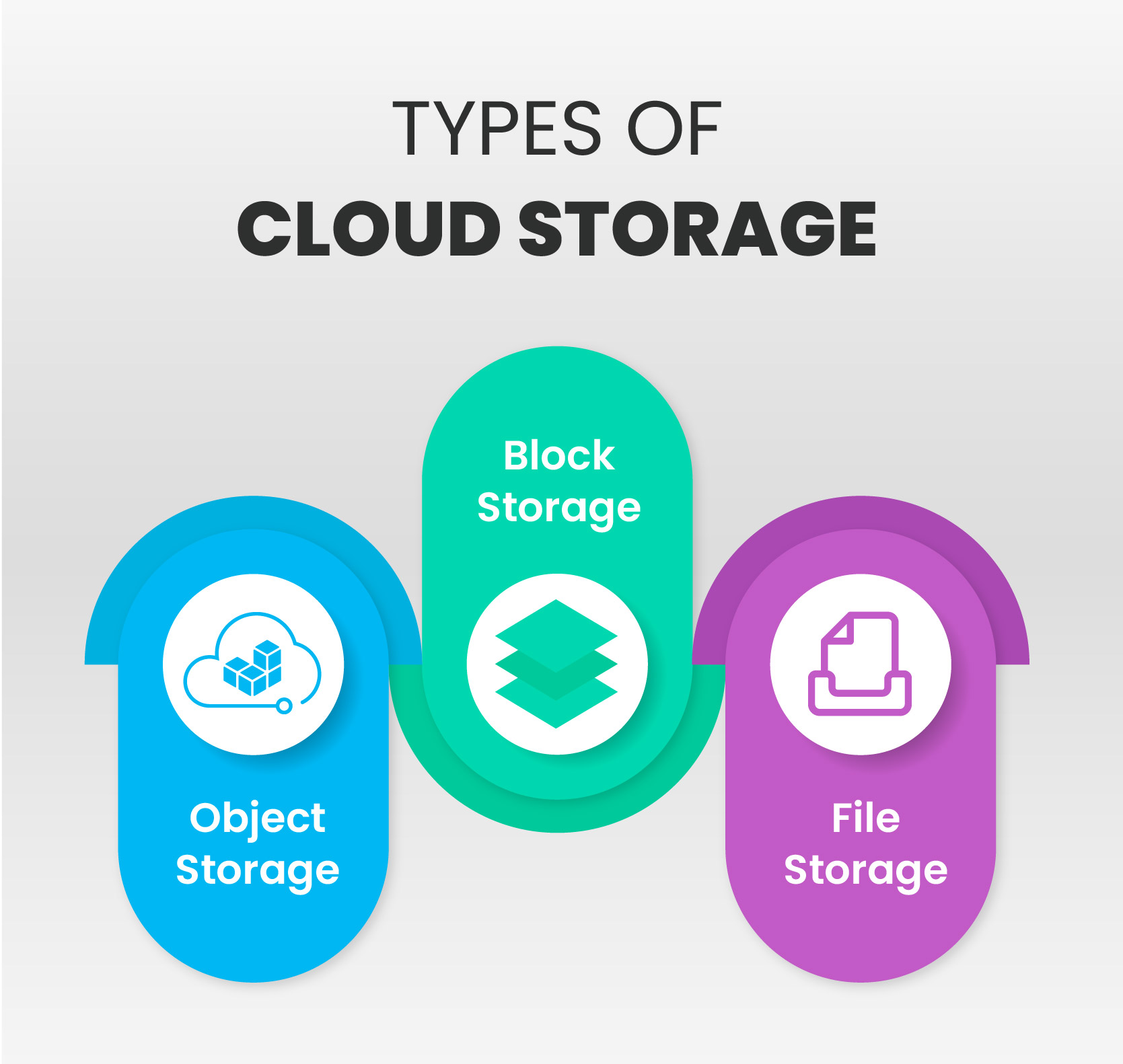
In addition, conformity laws such as the GDPR and HIPAA require data encryption as a way of safeguarding delicate info. Failure to abide by these criteria might result in severe consequences, making data encryption not just a security measure yet a legal need in today's electronic landscape.
Multi-Factor Verification Techniques
In boosting safety steps for global cloud storage services, the execution of robust multi-factor authentication approaches is important. Multi-factor verification (MFA) includes an extra layer of safety by calling for users to supply several kinds of verification before accessing their accounts, considerably lowering the risk of unapproved access. Typical aspects made use of in MFA consist of something the customer knows (like a password), something the customer has (such as a mobile phone for getting confirmation codes), and something the customer is (biometric information like finger prints or face recognition) By integrating these aspects, MFA makes it a lot harder for destructive stars to breach accounts, also if one variable is endangered.Organizations ought to additionally enlighten their customers on the significance of MFA and give clear directions on just how to set up and utilize it securely. By executing solid MFA techniques, organizations can substantially bolster the protection of their data stored in global cloud solutions.
Regular Information Back-ups and Updates
Given the essential role of securing information integrity in universal cloud storage space solutions through robust multi-factor authentication techniques, the following crucial aspect to address is making sure routine data back-ups and updates. Routine information backups are vital in mitigating the threat of data loss due to different aspects such as system failings, cyberattacks, or unintended removals. By supporting data consistently, organizations can bring back info to a previous state in situation of unforeseen occasions, therefore keeping organization connection and preventing significant disruptions.Moreover, staying up to date with software application updates and safety patches is equally important universal cloud storage Service in enhancing information security within cloud storage solutions. These updates usually have solutions for susceptabilities that cybercriminals may exploit to gain unapproved accessibility to sensitive information (universal cloud storage). By without delay using updates given by the cloud storage space provider, companies can enhance their defense devices and make certain that their information stays protected from evolving cyber hazards. Basically, regular information backups and updates play a crucial function in strengthening information safety steps and guarding vital info saved in universal cloud storage solutions.
Carrying Out Solid Access Controls
Gain access to controls are necessary in protecting against unapproved accessibility to sensitive data stored in the cloud. By implementing strong access controls, companies can ensure that just accredited employees have the essential permissions to watch, modify, or remove data.One efficient way to impose gain access to controls is by making use of role-based gain access to control (RBAC) RBAC designates certain roles to customers, approving them gain access to rights based on their duty within the organization. This technique ensures that customers only have accessibility to the data and functionalities called for to do their job responsibilities. Furthermore, executing multi-factor verification (MFA) includes an additional layer of safety and security by calling for individuals to provide several forms of confirmation before accessing delicate data.
Surveillance and Auditing Data Gain Access To
Structure upon the foundation of solid accessibility controls, effective tracking and bookkeeping of data gain access to is crucial in preserving information protection honesty within global cloud storage space services. Monitoring data gain access to entails real-time monitoring of that is accessing the data, when they are accessing it, and from where. By executing tracking systems, dubious tasks can be identified quickly, making it possible for rapid reaction to prospective safety violations. Bookkeeping data accessibility involves evaluating logs and records of data access over a specific duration to make certain compliance with security plans and guidelines. Regular audits assistance in recognizing any kind of unapproved accessibility efforts or unusual patterns of data use. In addition, bookkeeping information gain access to aids in establishing accountability amongst individuals and identifying any kind of anomalies that may indicate a safety and security risk. By combining durable surveillance devices with detailed auditing practices, companies can improve their data security position and reduce threats linked with unauthorized access or information breaches in cloud storage space atmospheres.Verdict
Finally, safeguarding data with global cloud storage space services is crucial for securing delicate information. By executing information encryption, multi-factor verification, normal back-ups, strong accessibility controls, and keeping an eye on information access, organizations can minimize the danger of information breaches and unauthorized gain access to. It is necessary to prioritize data security determines to make sure the discretion, honesty, and schedule of information in today's electronic age.Report this wiki page